Introduction
A while ago, I had a conversation with a former colleague about which information regarding an Azure tenant should be kept secure and which information is already publicly available – whether we like it or not.
While we agreed on most points, we had differing opinions about how secret a tenant ID should be.
In this post, I will explain why you shouldn’t spend time or effort trying to keep your tenant ID a secret. I will also show you how to find the tenant ID of any organization using nothing more than the domain.
Background
What is a tenant ID and why is it relevant to know it?
A tenant ID is the unique identifier that distinguishes your tenant from all other tenants in Azure. It is essentially a randomly generated GUID that Microsoft creates when the tenant is set up, and, like the tenant name, it is unique.
Why do you need to know it?
When working in Azure, you might be invited as a guest in multiple tenants. By getting into the habit of specifying the tenant ID, you ensure that you always connect to the intended tenant. If you are using a service principal, the tenant ID is mandatory for the connection.
Examples
Let’s look at some examples.
For these examples, we will use the following tenant ID: 3893bf31-4d67-4495-9c7e-41300de844dc.
Connect to a specific tenant using the PowerShell AZ module
When using the Azure PowerShell AZ module, this is the connect command you use to specify the tenant:
|
1 |
connect-azaccount -TenantId "3893bf31-4d67-4495-9c7e-41300de844dc" |
You can read my post about the AZ module for more information about that topic.
Connect to a specific tenant using the PowerShell Microsoft Graph module
We can do the same using the Microsoft Graph module where the commands are quite similar to those in the AZ module except for the fact that you define the scope of the connection.
|
1 |
Connect-MgGraph -Scopes "RoleManagement.Read.All" -TenantId "3893bf31-4d67-4495-9c7e-41300de844dc" |
So far, everything is simple – we have simply added -TenantId to the connect command, and we are ready to go.
Connect to a specific tenant using the Powershell Microsoft Graph module with service principal
Now, let’s try something more realistic and use a service principal for the connection. Notice that we need to get a token for the connection which requires us to identify the correct tenant ID.
Note: This is an example. Please don’t store the Client secret in clear text in any scripts!
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
$tenand_id = "3893bf31-4d67-4495-9c7e-41300de844dc" $body = @{ Grant_Type = "client_credentials" Scope = "https://graph.microsoft.com/.default" Client_Id = "82975134-df11-4d98-9bd0-5c5e5e89930e" Client_Secret = "X9M7Q~Ucq9wu_VflVBSnNDiArLtlF~OU5cgmO" } $connection = Invoke-RestMethod ` -Uri https://login.microsoftonline.com/$tenant_id/oauth2/v2.0/token ` -Method POST ` -Body $body $Token = $Connection.access_token Connect-MgGraph -AccessToken ($token |ConvertTo-SecureString -AsPlainText -Force) -NoWelcome |
How does it work?
The example above highlights one reason why some people argue that the tenant ID should be kept secret – since it is a value that could potentially be used during sign-in.
However, let’s debunk the idea that the tenant ID is actually a secret.
In each of the following scenarios, I will use my test domain with the domain name dev.mmt-consult.dk attached.
Find the tenant ID using a known domain
Let’s give it a try. All you need is PowerShell, a browser or any terminal that can connect to the internet.
We use the domain from earlier. To find the tenant ID, visit the OpenID configuration page which is used for collaboration with other organizations:
https://login.windows.net/Your-Domain/.well-known/openid-configuration
In this example, replace “Your-Domain” with the domain you want to retrieve the tenant ID from and open the page.
And voilà, the tenant ID is displayed in several attributes!
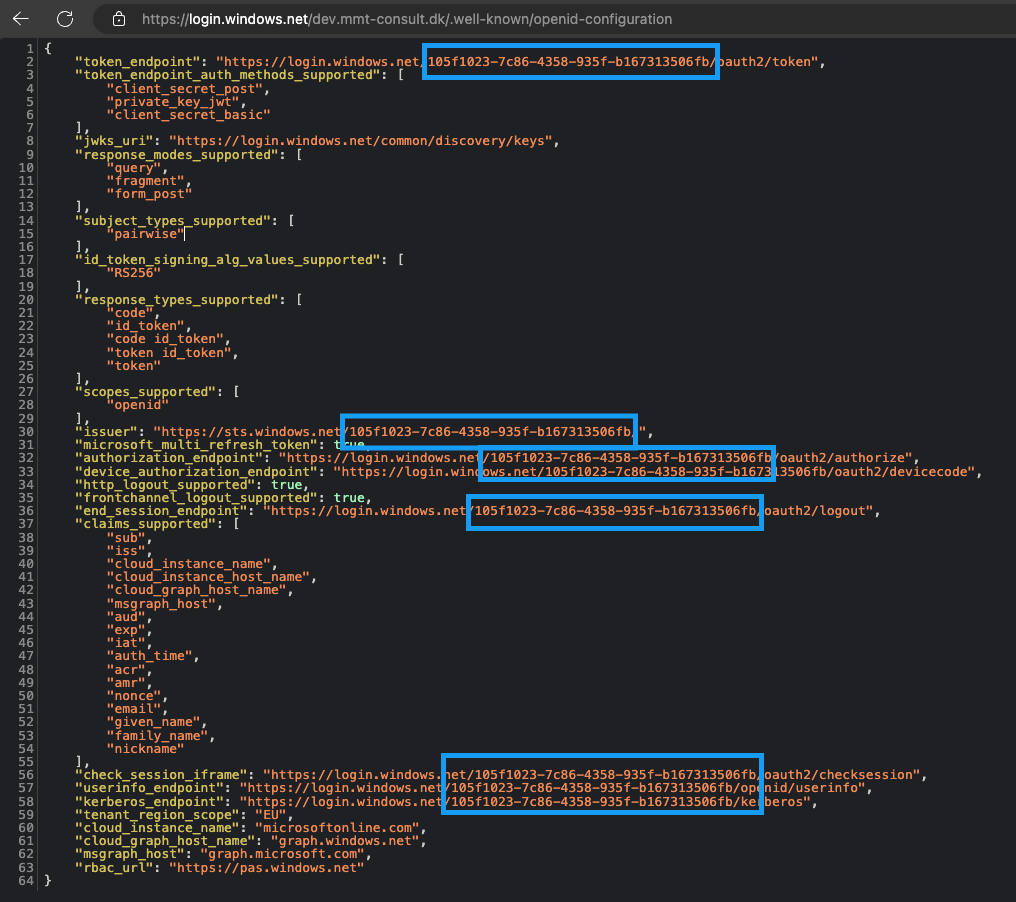
Using a web browser might be a bit tedious, so let’s script this process using PowerShell.
To do this, we need to specify the attribute which we target. In this case, we use the “userinfo_endpoint” attribute, although you can choose any of the marked attributes. The format will always be the same, which allows us to use the “/” character as a delimiter to extract our desired value.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
# Write the domain that you wish to look at $Domain = "dev.mmt-consult.dk" # Now, let's collect the data from Microsoft $openIdInfo = Invoke-RestMethod "https://login.windows.net/$($Domain)/.well-known/openid-configuration" -Method GET # In the end, we save and show the tenant ID in a variable named $tenantid $tenantid = $openIdInfo.userinfo_endpoint.Split("/")[3] For good measure, let's check that there is something in there. $tenantid # The next step is to use it to connect to a tenant using a module. # Let's use the AZ module for this example Connect-AzAccount -Tenant $tenantid |
That’s it! However, this doesn’t help us much, as we don’t have any credentials for this tenant. Nevertheless, the key takeaway is that it makes little sense to try and hide the tenant ID. In fact, if someone with malicious intent can’t figure this out, then you likely don’t have much to worry about from them at all.
Find the tenant name using the tenant ID
Let’s try to reverse the above. Suppose you have the tenant ID, but you don’t know the tenant’s name and would like to find it. (Note: This is not the domain name associated with the tenant, but the tenant’s name itself.)
While I haven’t found any public APIs that directly provide this information, the Azure portal offers a way to look it up. You could also use the developer tools in your browser, but honestly, there’s no need for that. Here is the process:
- Go to portal.azure.com and sign in.
- Open the Microsoft Entra ID blade.
- Now open External Identities.
- Find Cross-tenant access settings.
Click to add a new organization.
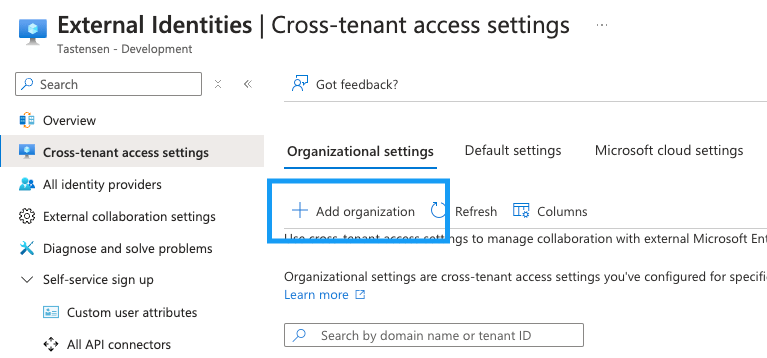
In the window that appears, enter the tenant ID of the organization you want to look up. Entra ID will perform a lookup and display the tenant name.
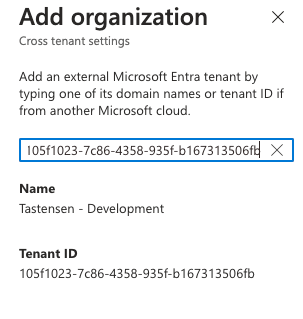
You don’t need to add the organization; simply typing the tenant ID will return the tenant name. As you can see, my dev tenant is named “Tastensen – development”.
Conclusion
In conclusion, trying to hide your tenant ID – something that is publicly accessible – is a futile effort and a waste of resources. These resources are better spent on more meaningful and impactful projects.





0 Comments